Sunny Jovita – 2301939046
Week 10
Disclaimer: This blog is for educational purposes only.
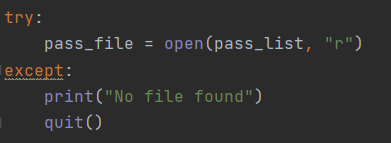
One of the most popular port scanning techniques is TCP half open port scan or sometimes refereed to as an SYN scan. This type of scanning is fast and sneaky since it tries to find the open ports on the target computer. Furthermore, it is hard to detect because it never completed the full TCP e way handshake. The scanner sends a SYN message and just notes the SYN-ACK responses. In short, the scanner doesnt complete the connection by sending the final ACK, it just leaves the target hanging.
Here, below I will show you how to see if the connection is open or closed.

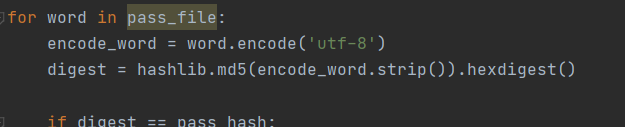
In the picture above, we can say that this is a SYN scan or TCP half open port scan. Why? because, as seen in the picture, from packet 7 until 19, it occurs between the source and target systems with these following steps:
Source = 192.168.223.171
Target destination = 192.168.223.172
Step 1
In packet number 7, 8, 9 the source starts sending a synchronization packet (SYN) to the server and waits for the target response.
Step 2
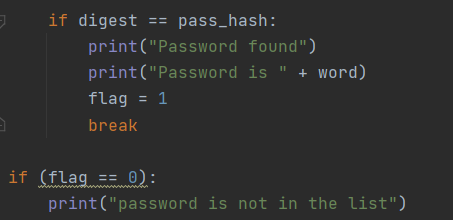
In the packet number 10, the target replies with a packet containing both an acknowledgment (ACK) and a (SYN) directed to the source and waits for the final ACK to arrive.
Step 3
However, as can be seen in the packet no 12, an RST is retrieved from the target. (in the packet no 11, the scanner/source doesn’t complete the connection by sending the final ACK, but it leaves the target hanging).
Conclusion
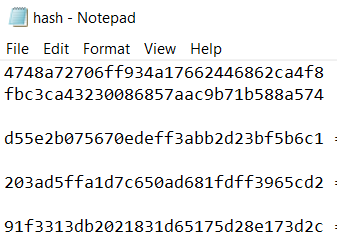
To summarize, from the packet no 10, 13, 19 SYN/ACK packets indicate that the port (5900) and (22) (127) are open. Rfb is for port 5900, and ssh is for port 22, and NETBIOS-ssn is for 137. However, in the packet no 12, an RST response appears and it means the port is closed, but the server is still alive. Those ports are considered open is a SYN packet is received a response.
Any SYN-ACK responses are possibly open ports. A RST (reset) response means the port is closed, but there is a live computer or device there. TCP half open scans are default scan in NMAP.